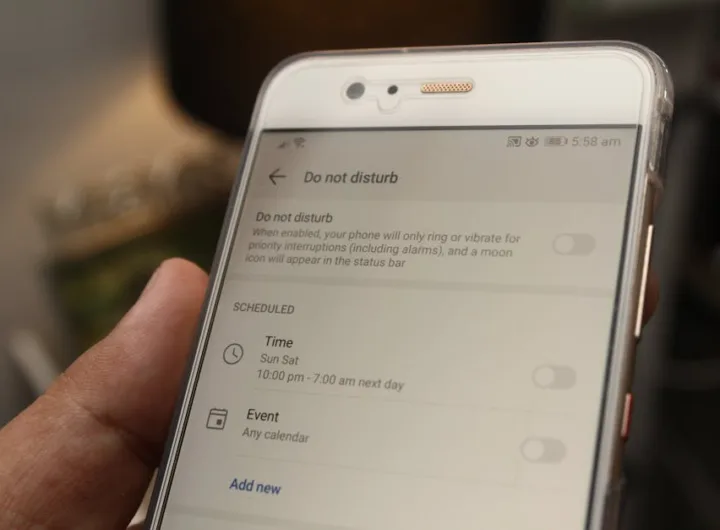
The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have integrated generative AI (GenAI) capabilities into their...
phishing
Nearly 40% of industrial enterprises worldwide now prioritize cybersecurity as a core operational requirement during digital transformation,...
In August 2024, cybercriminals executed one of the largest single-victim cryptocurrency thefts in history, stealing $243 million...
Despite significant investments in cybersecurity infrastructure, human error remains the leading cause of data breaches. A single...
Phishing remains one of the most persistent and effective attack vectors in cybersecurity, with attackers constantly refining...
Cybercriminals are increasingly exploiting Near Field Communication (NFC) technology to conduct large-scale fraud at ATMs and Point-of-Sale...
A new wave of malware targeting Apple devices has raised alarms among cybersecurity professionals. Dubbed “Infostealer,” this...
The UK has seen a surge in illegal sports streaming, with cities like Manchester and Newcastle leading...
Romance scams in the UK have seen a sharp 20% increase in 2024, with victims losing an...
Email accounts remain a prime target for cybercriminals due to their role in authentication, communication, and data...
A North Korean hacking group known as Elusive Comet has been exploiting Zoom’s remote control feature to...
A new wave of malware targeting iPhone users has raised alarms among cybersecurity experts. Dubbed “Infostealer,” this...
A new wave of highly convincing phishing emails impersonating Google has emerged, exploiting DKIM replay attacks and...
Cybercriminals and advanced persistent threat (APT) actors are abusing Cloudflare’s free tunneling service, “TryCloudflare,” to distribute remote...
Since early March 2025, Russian state-aligned threat actors have been conducting sophisticated phishing campaigns targeting organizations with...
The FBI has issued an urgent warning to Gmail and Outlook users about a surge in Medusa...
A new wave of malware targeting iPhone users has emerged, leveraging fake software updates and phishing campaigns...
The FBI has issued an urgent advisory warning Gmail and Outlook users about the escalating threat posed...
The UK has identified its worst cities for illegal streaming of Cheltenham races and top-flight sports, with...
The FBI and CISA have issued an urgent advisory (AA25-071A) warning users of Gmail, Outlook, and enterprise...