Red-Team News
The latest cybersecurity news, threat intelligence, and C2 development news enhanced by AI
1
 O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
 Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
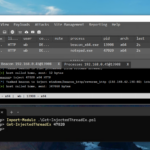
 Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
 Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
 Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
 O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
 Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
 Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
 Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
 Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
1
 O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
 Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
 Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
 Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
 Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
 O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
O2 UK VoLTE/WiFi Calling Flaw Exposes User Location via Call Metadata
2
 Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
Microsoft Resolves Linux Boot Issues Caused by August 2024 Windows Security Updates
3
 Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
Ivanti EPMM Zero-Days Exploited in Chained Remote Code Execution Attacks
4
 Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
Microsoft May 2025 Patch Tuesday: 5 Exploited Zero-Days and 72 Flaws Addressed
5
 Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues
Windows 11 KB5058411 and KB5058405 Updates: Security Fixes and Known Issues