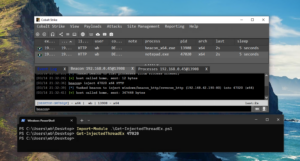
Cybersecurity researchers from Hunt have identified a server hosting advanced malicious tools, including SuperShell command-and-control (C2) payloads and a Linux ELF Cobalt Strike beacon. The discovery was made during a routine search for open-source proxy software, highlighting the risks of unsecured infrastructure and the sophistication of modern cyber threats1.
Key Findings
The exposed server contained multiple threat actor tools, with SuperShell and Cobalt Strike being the most prominent. SuperShell is a Python-based C2 framework offering SSH control, cross-platform payloads, and a web admin panel. The Linux ELF Cobalt Strike beacon was UPX-packed and masqueraded as jquery.com, connecting to 8.219.177[.]40:4432. The infrastructure included Huawei Cloud-hosted C2 servers (124.70.143[.]234) co-located with Asset Reconnaissance Lighthouse (ARL) for network mapping.
| Type | Indicator | Provider |
|---|---|---|
| IP | 124.70.143[.]234:8888 |
Huawei Cloud |
| File (MD5) | 91757c624776224b71976ec09034e804 |
UPX-packed SuperShell |
HTran and Rootkit Persistence
Additional analysis revealed HTran malware in the same environment, using process injection and rootkit techniques for persistence. HTran typically deploys via compromised web applications, installing itself in ProgramData and reconfiguring servers for RDP over port 80 to blend with HTTP traffic3. Debug errors in the rootkit component may expose C2 connections through log entries containing [SERVER]connection to [host]:[port] error.
Mitigation Strategies
Organizations should implement the following measures to defend against these threats:
- Patch management for web servers and cloud services
- Network monitoring for unusual ports (53, 443, 3306)
- PowerShell logging and application allow-listing
- Detection of
jquery.comcertificate mismatches
For SuperShell specifically, Hunt recommends monitoring port 8888/tcp traffic and analyzing UPX-packed binaries with the provided MD5 hash. Cobalt Strike Cat campaigns in South Korea have used similar infrastructure, with open directories on 144.48.4[.]219:8000 and C2 servers at 104.167.222[.]1064.
Relevance to Security Teams
The discovery demonstrates how threat actors leverage open directories for tool distribution. Security teams should prioritize scanning for exposed services and implement network segmentation. The UK NCSC’s 10 Steps to Network Security provides additional guidance for hardening infrastructure5.
Emerging threats in April 2025 include RansomHub delivered via SocGholish and AI-generated fake medical documents used in phishing campaigns. Chrome vulnerabilities CVE-2024-4671 (RCE) and CVE-2025-2783 (sandbox escape) also require attention.
Conclusion
This case highlights the importance of continuous network monitoring and threat intelligence integration. Organizations should update detection rules for SuperShell and HTran indicators while maintaining robust patch management programs. The combination of these tools in open directories suggests an evolving threat landscape where attackers increasingly rely on publicly accessible infrastructure.
References
- GBHackers. (2025). Researchers Uncover SuperShell Payloads and Various Tools in Hacker’s Open Directories.
- Hunt.io. (2025). Uncovering SuperShell and Cobalt Strike from an Open Directory.
- CISA. (2018). HTran Malware Analysis. AA18-284A.
- Hunt.io. (2025). Rust Beacon Delivers Cobalt Strike Cat.
- UK NCSC. (2025). 10 Steps to Network Security.