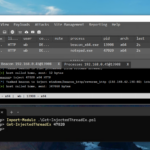
Red-Team News
The latest cybersecurity news, threat intelligence, and C2 development news enhanced by AI
1
 Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
 Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
 Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
 Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
 Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
 Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
 Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
 Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
 Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
 Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
1
 Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
 Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
 Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
 Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
 Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
 Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
Public Exploit Details Emerge for Critical Cisco IOS XE Vulnerability (CVE-2025-20188)
2
 Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
Apple Safari Fullscreen BitM Attack: Exploitation and Mitigation
3
 Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
Critical Unpatched Vulnerabilities in Versa Concerto Expose Systems to Auth Bypass and RCE
4
 Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
Critical SAMLify SSO Vulnerability Enables Admin Impersonation via Signature Wrapping
5
 Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)
Critical Privilege Escalation Vulnerability in WordPress Motors Theme (CVE-2025-4322)