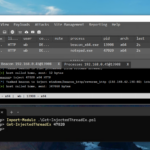
Red-Team News
The latest cybersecurity news, threat intelligence, and C2 development news enhanced by AI
1
 Exploiting Regex Filter Flaws for Remote Code Execution: Analysis and Mitigation
2
Exploiting Regex Filter Flaws for Remote Code Execution: Analysis and Mitigation
2
 Critical Vulnerabilities Patched in Mozilla Firefox and Thunderbird: Technical Analysis and Mitigation
3
Critical Vulnerabilities Patched in Mozilla Firefox and Thunderbird: Technical Analysis and Mitigation
3
 CVE-2025-45615: Critical Privilege Escalation Vulnerability in Yaoqishan Admin API
4
CVE-2025-45615: Critical Privilege Escalation Vulnerability in Yaoqishan Admin API
4
 Google Patches Actively Exploited Android System Vulnerability in May 2025 Update
5
Google Patches Actively Exploited Android System Vulnerability in May 2025 Update
5
 Microsoft Telnet Zero-Click Credential Theft Vulnerability: Technical Analysis and Mitigation
Microsoft Telnet Zero-Click Credential Theft Vulnerability: Technical Analysis and Mitigation
 Exploiting Regex Filter Flaws for Remote Code Execution: Analysis and Mitigation
2
Exploiting Regex Filter Flaws for Remote Code Execution: Analysis and Mitigation
2
 Critical Vulnerabilities Patched in Mozilla Firefox and Thunderbird: Technical Analysis and Mitigation
3
Critical Vulnerabilities Patched in Mozilla Firefox and Thunderbird: Technical Analysis and Mitigation
3
 CVE-2025-45615: Critical Privilege Escalation Vulnerability in Yaoqishan Admin API
4
CVE-2025-45615: Critical Privilege Escalation Vulnerability in Yaoqishan Admin API
4
 Google Patches Actively Exploited Android System Vulnerability in May 2025 Update
5
Google Patches Actively Exploited Android System Vulnerability in May 2025 Update
5
 Microsoft Telnet Zero-Click Credential Theft Vulnerability: Technical Analysis and Mitigation
Microsoft Telnet Zero-Click Credential Theft Vulnerability: Technical Analysis and Mitigation